To combat advanced attacks, it is crucial for security and risk management leaders to correlate data from the endpoint and elsewhere when threat hunting to offer efficient and secure remote access.
The latest 2021 Gartner’s Hype Cycle for Endpoint Security explores how chief information security officers can achieve their goals while reducing costs and improving visibility and control. It tracks the innovations that aid security leaders in protecting their enterprise endpoints from attacks and breaches.
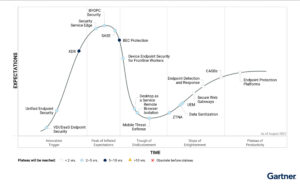
This year, the hype cycle prioritizes Unified Endpoint Security (UES) as the solution CISOs need to secure their endpoints. Based on discussions VentureBeat has had with chief information security officers and CIOs, the market momentum for Unified Endpoint Security is accelerating as cybersecurity teams rush to fill the gaps in their endpoint infrastructure and prevent potential security breaches before they occur.
According to Gartner, the global security software market grew by 10.3% in 2020 and reached 49.7 billion US dollars annual sales. The five largest segments with the highest growth rates are:
- application security testing
- access management
- endpoint protection platform (enterprise)
- secure email gateways
- identity governance and administration
The Endpoint Protection Platform (Enterprise) category is the second-fastest-growing segment of the global security market, generating $ 8.8 billion in 2020 (and 20% CAGR). The five largest providers are Microsoft, McAfee, Norton LifeLock, IBM and Broadcom.
Key Take-Aways
This Hype Cycle’s most helpful advice comes from its ideas of orchestrating unique applied sciences to give chief data safety officers, CIOs, and cybersecurity teams proper-time threat evaluation and asset management data interior a single data lake.
Here are some of the key insights from Gartner’s Hype Cycle for Endpoint Security, 2021, according to VentureBeat:
- Gartner is seeing a rise in zero-trust network access (ZTNA) initiatives across their enterprise clients today. The Hype Cycle’s finding on zero trust is consistent with what chief information security officers tell VentureBeat about their zero trust roadmaps, pilots, and plans. In almost every conversation VentureBeat has with chief information security officers in financial services and manufacturing, zero trust is first mentioned as a business decision. Scaling endpoint security across new digital revenue models is the goal. Even before President Joe Biden’s Executive Order on Improving the Nation’s Cybersecurity, 160 cybersecurity vendors claimed to have zero trust-based products and cloud services. According to Gartner, interest in zero-trust continues to outpace the broader cybersecurity market, growing more than 230% in 2020 over 2019.
- ZTNA products’ scale has expanded beyond web applications to support a broader range of applications and protocols, illustrating a quickening pace of innovation. Gartner notes that the current generation of ZTNA applications has improved user experiences, increased flexibility, and improved persona and role-based adaptability. Gartner also notes that “cloud-based ZTNA offerings improve scalability and ease of adoption.” Absolute Software’s acquisition of NetMotion is prescient in positioning the combined companies to deliver what CISOs are looking for in a ZTNA solution. Other companies in the ZTNA space to watch include Ericom — which provides for ZTNA and other technologies in the cycle, such as remote browser isolation, secure web gateway, and CASB — in its ZTEdge Zero Trust Cloud Security platform. Ivanti Neurons for Zero Trust Access uses machine learning to streamline security policies, compliance, and least-privileged access across users, devices, and applications to ensure network micro-segmentation is in force. Additional ZTNA vendors to watch are Akamai, Appgate, Cato Networks, Netskope, Perimeter 81, Proofpoint, and SAIFE.
- Unified endpoint management (UEM) earns respect during the pandemic and sees adoption increase. UEM proved its value during the pandemic by unifying identity, security, and remote access in support of ZTNA architectures now considered essential for securing an anywhere workforce. Like ZTNA, there’s been rapid innovation occurring in UEM over the last 12 to 18 months, with the goals of reduced security and compliance risks, along with support for more devices and operating systems. UEM’s benefits — which include streamlining continuous OS updates across multiple mobile devices and platforms, enabling device management, and having an architecture capable of supporting a wide range of instruments and operating systems — are why enterprises are looking to expand their adoption of UEM. Another significant benefit enterprises mention is automating internet-based patching, policy, and configuration management. UEM leaders include Ivanti, which provides its customers with additional security solutions integrated into its UEM platform, including passwordless multifactor authentication (its Zero Sign-On feature) and mobile threat defense (MTD). Other vendors to watch in UEM include Blackberry, Citrix, and Sophos.
Gartner’s latest Hype Cycle for Endpoint Security makes a case for unified endpoint security being a vital platform for bringing together the diverse parts of tomorrow’s cybersecurity tech stack. Endpoint security vendors need to accept the challenge and step up their pace of innovation to slow down ransomware and worse cyberattacks that are reaching record levels this year.
Endpoint security? No problem.
Given the rapid growth of virtual meetings, remote training sessions, and sales calls, securing virtual desktop infrastructure (VDI) and desktop-as-a-service (DaaS) connections has become a priority over the last two years – and we can help. You can talk to us about how to prevent virtual sessions from being hijacked while securing the identity of every virtual participant. Our on-demand cybersecurity service is an effective way to assess, remediate, and implement a robust cybersecurity program. Please send us an email via info@puttiapps.com to know more about our service.

